Almost a year ago I wrote about defraging drives from the command line.
I got an email from John that week:
“Hi Steve, I wanted to let you know about a free defragmentation tool. It is called UltraDefrag. It can defrag drives, Registry hives, and the paging file”
It took me a while, but I just checked it out – and it is a great tool.
Almost every feature of it can be called from the command line using the command line interface.
The drive and file defrag shows the blocks it is moving (Reminiscent of the old Norton defrag)
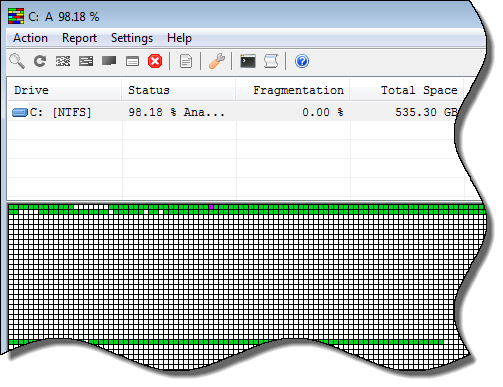
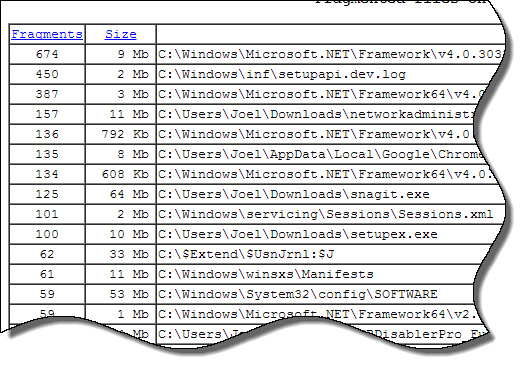
After your defrag is complete you can get an HTML report of its progress:
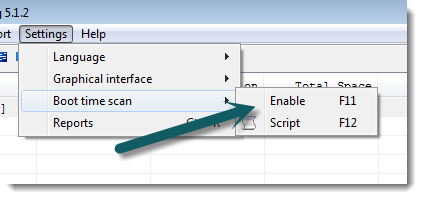
If you want to scan files in use (Like the registry hives, and the paging file) you can enable a boot time scan:
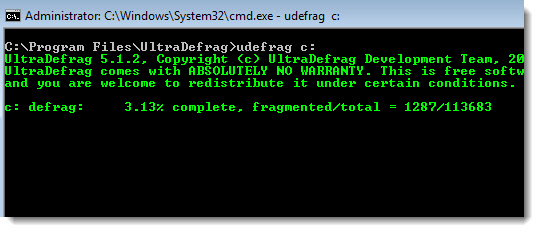
To show you how easy it is to run from the command line, here are some simple examples:
Defrag the C Drive:
udefrag.exe c:
Defrag a specific file and folder:
udefrag C:\Windows\WindowsUpdate.log “C:\Program Files”
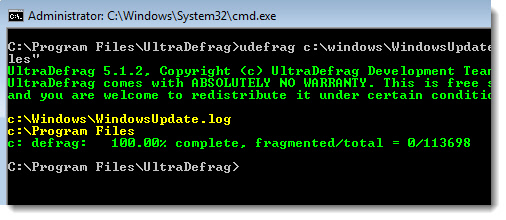
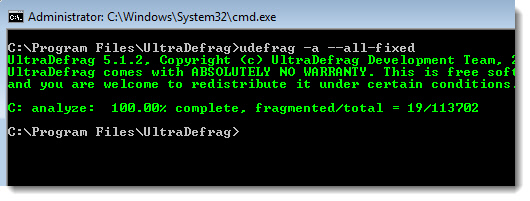
Analyze all drives (Don’t defragment):
udefrag -a –all-fixed
Get your copy of UltraDefrag from here:
http://ultradefrag.sourceforge.net/en/index.html?download
One more thing…Subscribe to my newsletter and get 11 free network administrator tools, plus a 30 page user guide so you can get the most out of them. Click Here to get your free tools

{ 4 comments… read them below or add one }
Thanks for the tip steve. Great stuff.
Thanks for the info steve, I have been looking for something like this for a while. Thanks for telling us about it.
I am trying to defrag my hard drive without admin privileges. Is there any
way either registry or policies that can give the local user the privileges
to defrag their hard drive on their own? Any help would be greatly appreciated.
Hello Ramesh,
By its nature it requires full admin rights. This is because defrag needs to have low level access to the hard drive. I would say unless you have someone write a program to proxy it for you as an administrator…defrag must be run by a local admin.
One way around it would be to setup a scheduled task that ran at specific intervals, and then saving the admin password into the task. That way users without the rights have no need to call it (It is running in the background)