Since the release of Windows XP SP2 file and printer sharing has been blocked by default in the Windows firewall. This includes all versions of Vista, and even XP SP3. Heck the same is true for the pre-release versions of Windows 7 that I have looked at.
This creates a problem for many of our tools and products. For example, our remote USB disabler cannot do its work without remotely writing the appropriate registry keys. Our Remote Control product cannot automatically install its agent without file and printer sharing. They all use this to do their magic. We are not the only ones – psexec from SysInternals needs file and printer sharing too.
There are hundreds if not thousands of tools used by IT administrators that require file and printer sharing enabled in the firewall.
If you have 10 computers it is an easy fix. You simply walk around to each of them and add an exception in the firewall. Simple. Done.
If you have 100s of computers spread across 3 states…you now have a much more difficult problem. You could write a script that executes at login. The trouble with this idea is that every user would need full administrator access to their own machine. This type of access is getting pretty rare these days, so I don’t even consider it an option.
The best method is group policy. I am going to walk you through it. My example uses Windows 2003 Server. Those of you with 2008 will find that it is almost exactly the same. If you have 2000 Server…well…you have your hands full anyway and shouldn’t even have time to read this article.
Start out by getting on your domain controller. Open “Active Directory Users and Computers”. You need to determine what group of machines your policy is going to be applied to. Some organizations will have computers under many different OUs.
To keep things simple I am going to change the group policy for the entire domain.
Right click on the domain name and go to properties:
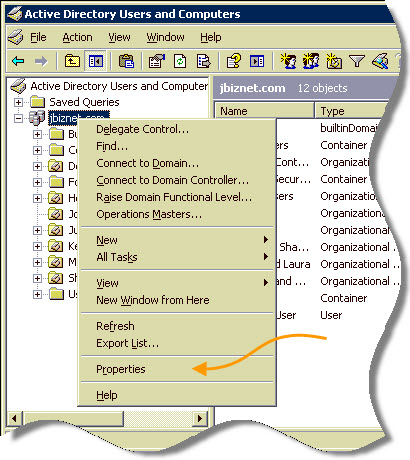
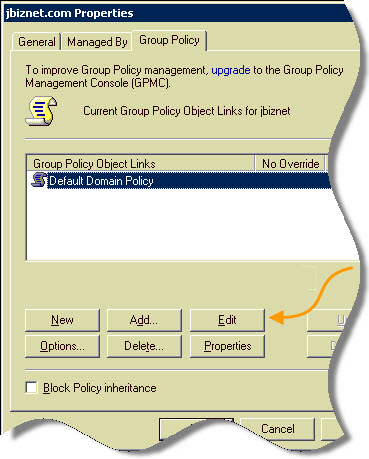
This will bring up a properties window. You will want to move to the Group Policy tab, select the policy you want to edit (In our case it is the Default Domain Policy) and press the edit button.
This is a computer policy (It will apply to computers…not specific users), so drill down to:
Computer Configuration -> Administrative Templates -> Network -> Network Connections -> Windows Firewall
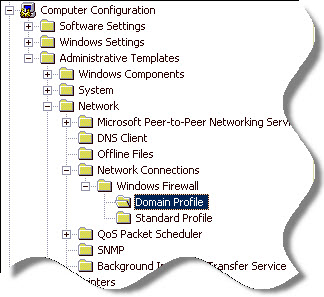
You will notice two sections under this area. A domain profile, and a standard profile. A machine will automatically determine which profile it should use by the type of network it is connected to. Directly from Microsoft, they are defined in this way:
* Domain profile The domain profile is the set of Windows Firewall settings that are needed when the computer is connected to the managed network. For example, the domain profile might contain settings for excepted traffic for the applications and services needed by a managed computer in an enterprise network.
* Standard profile The standard profile is the set of Windows Firewall settings that are needed when the computer is connected to another network. A good example is when an organization laptop computer is taken on the road and connects to the Internet using a public broadband or wireless Internet service provider. Because the organization laptop computer is directly connected to the Internet, the standard profile should contain more restrictive settings than the domain profile.
So generally speaking, I suggest only making these changes to the Domain Profile. You don’t want your sales guys hooking up to a hotel network with their file and printer sharing fully accessible.
Selecting the domain profile, and looking on the right we see what we need – “Windows Firewall: Allow file and printer sharing exception”
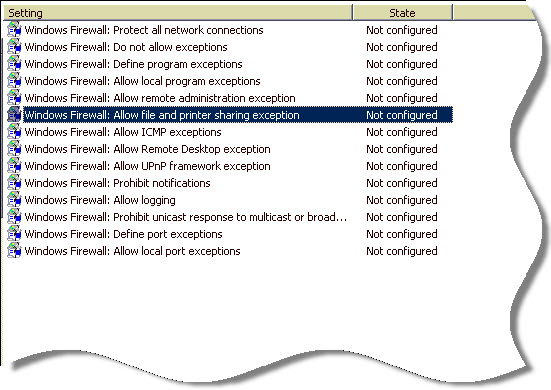
There are two items you need to set. First check the radio button to enabled, and then below you need to fill out a filter value. This tells the group policy what computers are allowed to connect to the machine. For our example I will put *
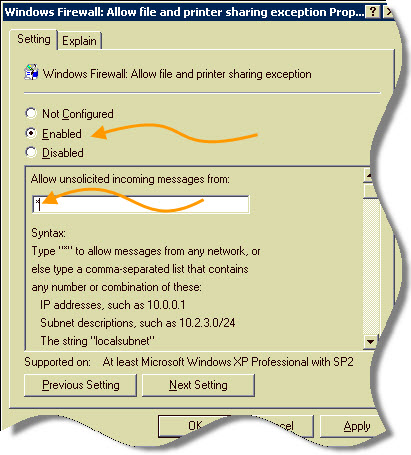
This value allows any computer to connect. Click OK, and allow some time to pass (15 to 30 minutes). Then your computers will pick up the new policy. If you are impatient you can go to the command line on the server and your test machine. Type: GPUPDATE /force
If I hop on one of my Vista machines we can see that it has accepted the policy:
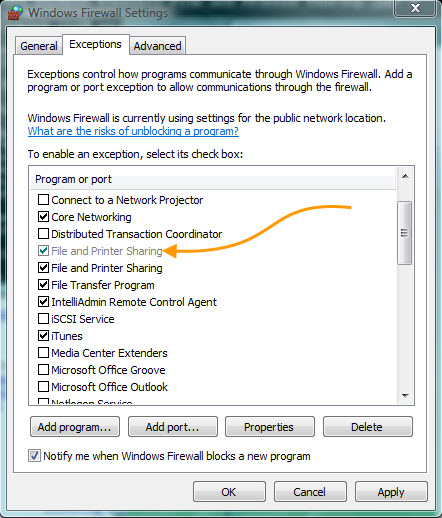
Perfect. Now I can terrorize my programmers by rebooting all of their machines at the same time using Network Administrator 🙂
One more thing…Subscribe to my newsletter and get 11 free network administrator tools, plus a 30 page user guide so you can get the most out of them. Click Here to get your free tools

{ 3 comments… read them below or add one }
Your solution doesn’t prevent users with administrator rights from getting “File and Printer Sharing for Microsoft Networks” unchecked on network card. If they do that you have back these machines unmanagable 🙂
True. But that problem is much tougher to crack. I believe the only way of automating that issue is to iterate through each network card in the registry and enable on each – not fun when Microsoft constantly is moving things around for each version of Windows.
I’ve gone through these steps updated the group policy due to my impatience, but I don’t understand why when I go and check the test machine firewall the “Only this network (sub-network)” is chosen by default despite using *